This chapter is part of the Fraud Fighters Manual, a collective set of stories from Fintech fraud fighters. Download your copy of the Fraud Fighters Manual here to read the full version.
Chapter 1: Know Your Fraudster
“The most important thing is to be aware of the types of fraud that exist and to be very vigilant about putting human effort into analysis and critical thought.” - Robert Reynolds, Pinwheel
Fraud and fraudsters come in many flavors. First party and third party. External and internal. Some are driven by opportunity—while others carefully plan their attack. But every type of fraudster relies upon a veil of deception. Once that deception is pierced, the threat is mitigated.
Know Your Customer (KYC) and Know Your Business (KYB) regulations provide guidelines through which organizations can better identify potential fraudsters and better protect themselves against the financial disruption of fraud.
Fraud is Everywhere—and Difficult to Defend Against
Fraud is on the rise. According to PwC’s Global Economic Crime and Fraud Survey 2022, 51% of responding organizations reported experiencing fraud within the last two years, the highest level in 20 years. In its 2023 Fraud and Industry Trends, LexisNexis attributes rising fraud to various societal accelerants, including digital transformation, increased automation, and disruptive new technologies.
But organizations are not helpless. Behind every fraud, there’s a person. By understanding—and identifying—fraudsters, an organization can develop its first and most critical line of defense.
The average US Fintech loses $51 million to fraud every year.
In 2022, PYMNTS and Ingo Money surveyed 200 Fintech executives in the United States and discovered that the average Fintech company loses $51 million to fraud every year. The same report revealed that 47% of Fintechs believe that fraud is their most pressing challenge.
We interviewed Robert Reynolds to learn more about fraudsters, how they operate, and how they can be detected through advanced KYC/KYB processes. Robert Reynolds is the Head of Product at Pinwheel (pinwheelapi.com), a B2B company that helps facilitate connectivity between institutions and payroll systems. Pinwheel’s mission is to enable greater financial outcomes for end consumers by creating greater access to credit—and simplifying data-sharing patterns between consumers and financial institutions.
Robert has spent 15 years focused on lending, Fintech, consumer lending, and banking-as-a-service. His fraud-related knowledge extends to unsecured business loans, auto loans, and credit loans across the US, UK, Australia, and Canada.
The Many Types of Modern Fraud
How do you defend yourself against an attack when you don’t know where it will come from—or who it will be? There are many types of fraud, perpetrated by many types of fraudsters. The modern organization faces global exposure and rising advancements in tech.
First-party vs. Second-party vs. Third-party Fraud
According to Robert, one of the most important things a company can do to identify bad actors “is to be aware of the types of fraud that exist.” Based on that knowledge, organizations can then develop dynamic policies to stop fraud in its tracks.
Fraud is frequently categorized as first-party or third-party, depending on how the fraudster presents their identity. In 2021, the Federal Trade Commission received close to 1.4 million reports of identity theft from customers.
- First-party fraud. A fraudster knowingly misrepresents themselves or their actions for material gain. A car salesman sells a car that they know will break down in a few days—and tells the customer that there’s nothing wrong with it. An executive writes a large check they know will bounce to secure a contract. Robert points out that “in a lending environment, it’s sometimes called friendly fraud as well.”
- Third-party fraud. A fraudster uses someone else’s personal information for material gain. “It can manifest primarily digitally—in the form of information gleaned from the dark web or stolen information from phishing websites—but it can also manifest physically in the real world,” says Robert. An identity thief uses someone else’s information to procure a car loan, which is then never paid. Or they pretend to be an executive and write a large check to themselves.
With the right identity verification processes in place, organizations can detect fraudsters in all shapes and forms to prevent attacks from taking a serious toll.
The 7 Fraudster Archetypes
Fraudsters differ in origins and levels of premeditation. A fraudster could be a teenager idly trying out Social Security numbers they purchased online—or a well-planned group of malicious attackers for whom committing fraud is their day job.
There are likely hundreds of thousands of fraudsters out there. But they tend to fit into one of seven major categories.
1. The Thief
Environment: External
Premeditation: None
Fraud Type: First-party
The Thief is an impulsive individual generally conducting a reckless, one-off fraud. A young partier discovers a credit card on the dance floor and uses it to buy just a few drinks. An employee sees a coworker’s phone unlocked—and takes the opportunity to Cash App themself hundreds of dollars.
Thieves act when the opportunity arises. But any time an opportunity does arise, the Thief might be there. They can be thwarted by most rudimentary identification checks.
2. The Con Artist
Environment: Internal or External
Premeditation: Moderate
Fraud Type: First-party
The Con Artist lies to get their way—whether they have privileged information or not. A person walks into a bank and insists that the ATM short-changed them, getting the teller to hand over money that they weren’t actually owed. A vendor says they haven’t been paid, even though they were.
Con Artists exploit human nature by lying about their identity and situation. They are defeated through checks and balances. The proper systems and processes make it harder to manipulate an individual.
3. The Disguise Artist
Environment: External
Premeditation: Moderate
Fraud Type: Third-party
The Disguise Artist uses another person’s identity to give themselves access to resources. A cybercriminal sends out an email as a C-suite executive to have an executive assistant wire them money. A vendor forges paperwork stating that a former partner agreed to a contract that was never actually negotiated.
Disguise Artists don’t usually have any familiarity with the individual whose identity they are stealing. Rather than having privileged information (such as a Social Security number), they use social engineering and confidence tricks. Identity verification and processes will quickly reveal their deception.
4. The Impersonator
Environment: Internal or External
Premeditation: Moderate
Fraud Type: Third-party
The Impersonator misrepresents who they are for profit—and they usually have a plan. A parent with a bad credit score uses their child’s identification to open a credit account. A business owner forges their partner’s signature on documents to take out loans.
An Impersonator goes a step further than the Disguise Artist by using actual personally identifiable information to pretend to be someone. Thus, it’s not enough to simply verify that an “identity” is real; to protect against an Impersonator, you must also verify that the person is who they say they are. This is particularly difficult in the case of family fraud, as relatives are frequently able to take on an identity quite easily.
When fraud comes from inside the household.
“Family fraud is when you have someone who is very close to the victim and can easily represent their identity, misrepresenting the state of their interest or needs,” says Robert. “And that could be a spouse, caregiver, or another family member.”
5. The Opportunist
Environment: Internal
Premeditation: None
Fraud Type: First-party
The Opportunist exploits ad hoc processes or system vulnerabilities. A retail investor realizes that a stock trading app is giving them free stocks every day, instead of once, and continuously exploits the error. A vendor sends fewer inventory items in a shipment after noticing they haven’t been counted.
An Opportunist does not misrepresent who they are—and they don’t set out to commit fraud or even thievery. Rather, they take advantage of exploits that already exist to get away with small things that they should not. To identify Opportunists, not only does identity need to be tracked, but also behavior.
6. Organized Criminals
Environment: External
Premeditation: High
Fraud Type: Varies
The Organized Criminal is working with a professional team. An organized cyber-criminal gang conducts a DDoS attack on a cryptocurrency exchange with the goal of gaining access to the system. A ring of multiple identity thieves represents itself as a business to a bank, walking away with a sizable loan.
Organized Criminals have resources. They are extremely dangerous but comparatively rare. They have the tools and processes to conduct significant damage—but they can be defeated by the same identity-driven protocols as other types of fraudsters.
7. The Shady Business
Environment: External
Premeditation: High
Fraud Type: Varies
The Shady Business is a business knowingly operating outside of regulatory compliance or even the law. A company pushes forward with a project that will incur major environmental compliance issues. A business deals with individuals that it knows are committing fraud or forgery.
Shady Businesses bring risk to banks and other financial institutions. Organizations have to vet and monitor their business relationships in addition to their customer relationships to avoid financial and legal consequences.
Know Your Customer (KYC) and Know Your Business (KYB) Strategies
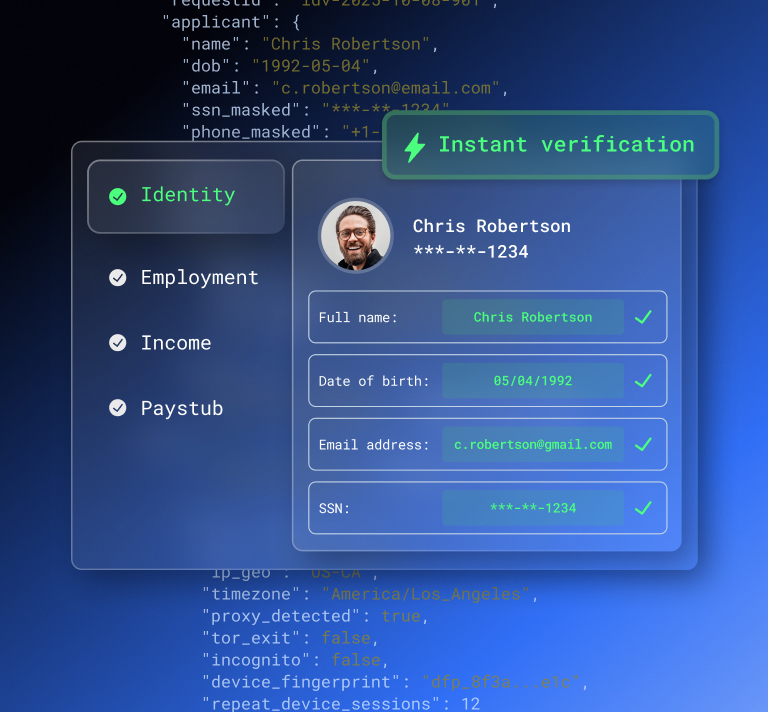
Once you know your fraudsters, it’s time to detect them—through identity verification and due diligence. KYC/KYB regulations form the framework of the necessary standards and processes.
Know Your Customer
KYC is a regulatory requirement for financial institutions. Fintech companies, banks, and credit unions must identify individuals before taking them on as customers. KYC strategies protect against the Disguise Artist, Impersonator, and Organized Criminals.
Compared to KYB, KYC is fairly easy to implement. Under KYC, you must:
- Collect (and protect) personally identifiable information (PII).
- Process the information internally.
- Confirm that the information is valid and accurate.
Robert highlights the importance of constantly revising KYC strategies, particularly when dealing with third-party fraud. “You’re effectively fighting against an enemy with unlimited time and unlimited resources,” he says. “The idea that they’re not going to change their strategies in response to your tactics is somewhat foolhardy. You need dedication to updating and changing.”
For most customers, identity verification processes are easy to manage and well-tolerated. For financial institutions, solutions are available to manage and streamline the verification process end to end.
Know Your Business
KYB refers to the process of verifying any vendors or business entities that the organization does business with. KYB strategies are harder to implement because they require a higher level of due diligence. As Robert points out, “in the case of KYB, where you’re verifying the legitimacy of a company to assess the risk of doing business with them, that’s more acutely associated with the actual legitimacy of the business. In that sense, just meeting the bare minimum of the legal requirement is not going to be nearly enough to actually prevent and mitigate fraud.”
Under KYB, organizations must collect and process large volumes of data. They must investigate and confirm the company’s financial, legal, and regulatory compliance information—and they must complete background checks on major stakeholders. In short, “KYB success relies very, very heavily on governance and process control to ensure compliance,” Robert says.
KYB strategies protect financial institutions from large-scale fraud, such as those conducted by Organized Criminals or the Shady Business. Critically, KYB prevents a financial institution from doing business with a company that could be otherwise involved in breaking the law.
Frictionless Fraudster Management
All fraudsters have something in common: they are lying. A fraudster misrepresents who they are, what they want, or what they can provide. Confirm all the facts to understand the end game of the fraudster—and to prevent them from getting what they want.
Today, it’s not enough to simply meet the standards of KYC/KYB regulations. Companies must use all available data to identify the most clever fraud instances.
Advanced KYC/KYB Strategies
Robert points out that “if you want no fraud, you’ll have no volume run through your business.” Reducing fraud frequently means adding friction—and adding friction reduces volume. But there are complex KYC/KYB practices that operate behind the scenes, effectively identifying the hallmarks of fraud before the fraud is realized and friction created.
For KYC, companies can use contextual and behavioral clues to identify potential fraud. Is a new device being used? Is the user in a new location? Is the email address new? Is the phone number verified? These are clues passively collected without interruption to the customer.
“This requires true human intervention, like evaluating and categorizing fraud into different categories and coming to good definitions,” Robert explains. “And being diligent about sampling enough of your consumer data to not just trust the definitions you have in place but staying vigilant and trying to observe new types of fraud.”
For KYB, companies have to be more discerning. They need to use third-party solutions to ensure that the business isn’t just active—but that it’s trustworthy. And like advanced KYC policies, the best KYB strategies use behavioral modeling and real-time detection. Are unusual behavioral patterns occurring under the account? Is the account asking for something it has never asked for before?
The behavioral hallmarks of fraud.
“I know what a good customer looks like, how they act, how much time they spend doing things, how often, and in which ways they communicate with me,” says Robert. “And I think one of the hardest things for fraudsters to determine is what that profile of a normal consumer looks like and to mirror it.”
Key Takeaways:
- There are many types of fraudsters, with varying degrees of organization and competency.
- On both a customer and business level, your goal is to catch bad actors while letting good actors through—as seamlessly as possible.
- Using advanced KYC and KYB strategies like behavioral modeling and real-time detection paired with continuous human intervention are critical steps for success.
It is one thing to be aware of the various types of fraud and the fraudster archetypes involved.
But the challenge comes in dissecting and then piecing together who someone truly is and whether they are who they say they are. Find out what happens in the next chapter by downloading your copy of the Fraud Fighters Manual here.



.svg)
.svg)